这是一个创建于 2313 天前的主题,其中的信息可能已经有所发展或是发生改变。
起因
水平不够,折腾了一天的 iptables 规则还是没获得自己想要的效果。 把自己目前的状况写下来希望有大佬能指点一二……
详情
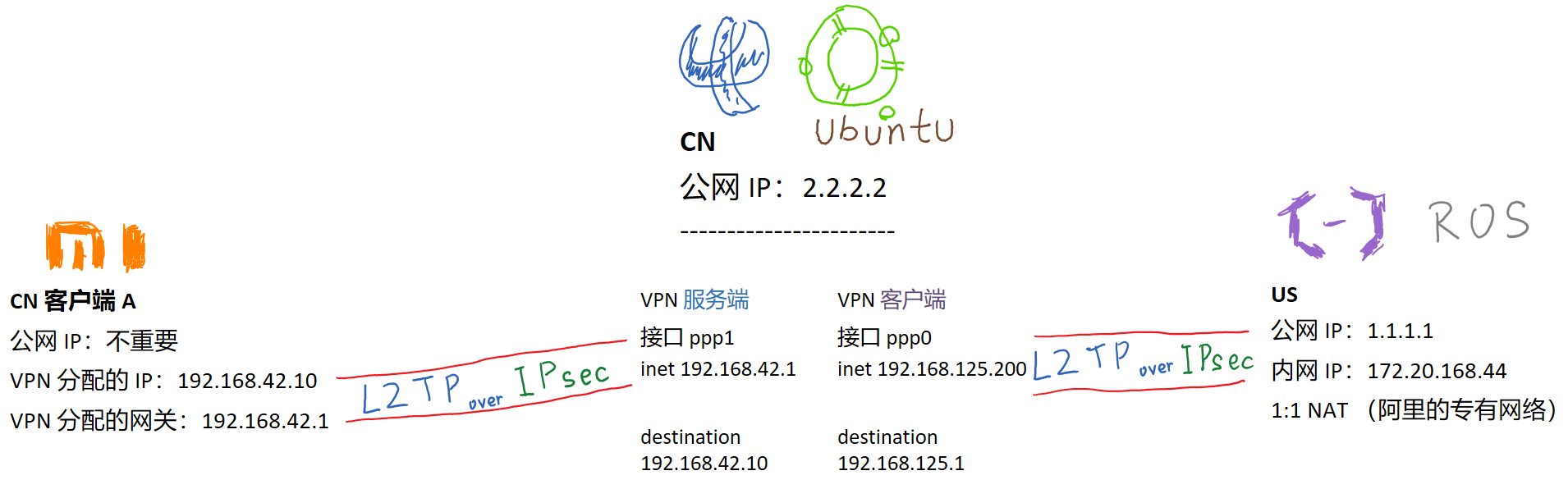
见图。
目标就是国内外分流 CN 客户端 A 连上 VPN 之后,国内 IP 段从 eth0 走,国外 IP 段从 ppp0 走。
有用的信息和遇到的问题
如上图全部 VPN 建立连接后。
- 从 CN 客户端 A 进行 ping 测试:
- 从 CN 客户端 A 访问网页:
192.168.125.1 [US 服务器 VPN 服务端网关] 成功访问 RouterOS 的管理页面
172.20.168.44 [US 服务器 eth0 IP] 成功访问 RouterOS 的管理页面
...
正常网站均能打开。
不存在的网站均无法打开。
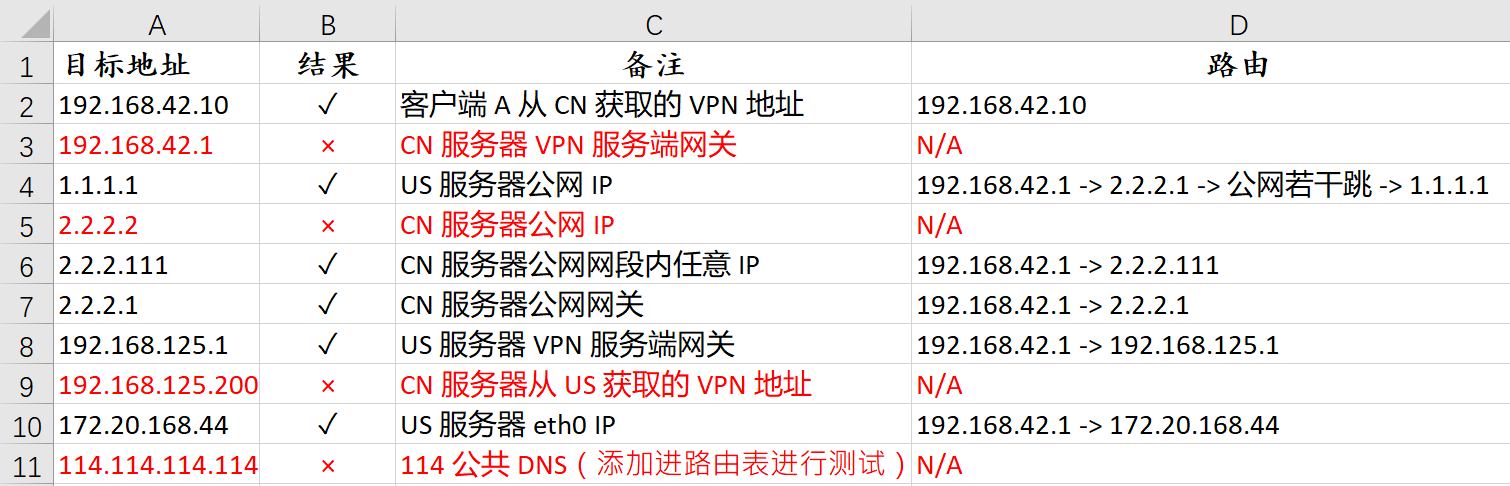
- 从 CN 服务器进行 ping 测试:
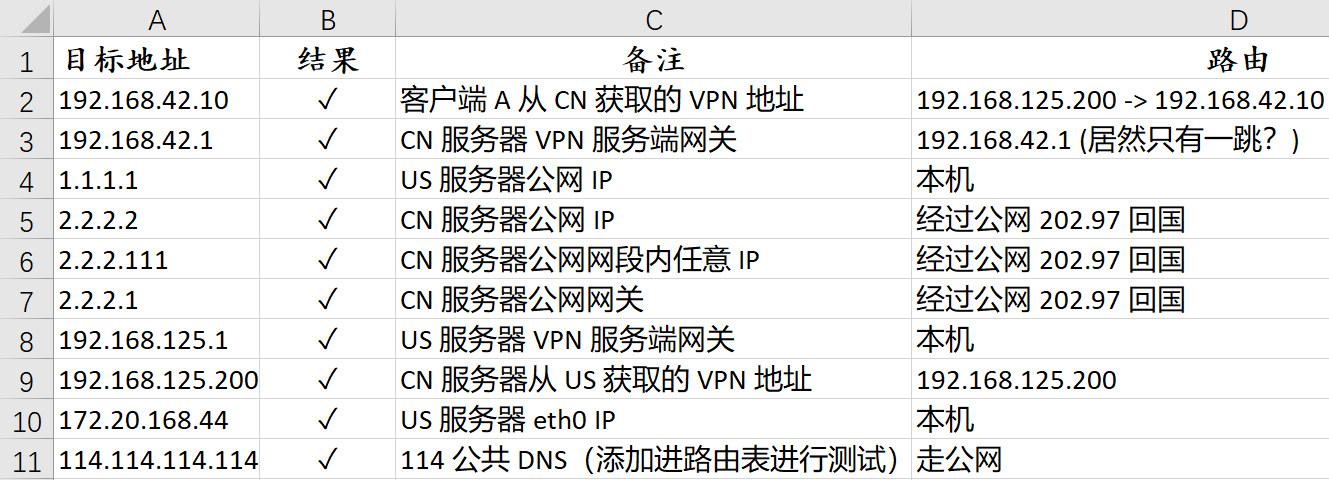
- 从 US 服务器进行 ping 测试:
-
CN 服务器路由表
使用 ip route add 命令添加。
default via 2.2.2.1 dev eth0 onlink ( eth0 默认公网路由)
114.114.114.0/24 via 192.168.125.1 dev ppp0 (临时设置测试连通性)
172.20.168.0/24 via 192.168.125.1 dev ppp0 (临时设置测试连通性,US 内网 IP 段)
172.217.0.0/16 via 192.168.125.1 dev ppp0 (临时设置测试连通性,Google)
192.168.42.10 dev ppp1 proto kernel scope link src 192.168.42.1 ( ppp1 默认路由)
192.168.125.1 dev ppp0 proto kernel scope link src 192.168.125.200 (ppp0 默认路由)
2.2.2.0/24 dev eth0 proto kernel scope link src 2.2.2.2 ( eth0 默认公网路由)
-
US 服务器路由表
-
CN 服务器 iptables 规则
-
filter
-
Chain INPUT (policy DROP 74 packets, 5196 bytes)
pkts bytes target prot opt in out source destination
36215 2419K f2b-sshd tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 22
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1701 policy match dir in pol none
11619 569K DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
271K 38M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
18 7456 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 500,4500
8 776 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1701 policy match dir in pol ipsec
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1701
18873 1404K ufw-before-logging-input all -- * * 0.0.0.0/0 0.0.0.0/0
18873 1404K ufw-before-input all -- * * 0.0.0.0/0 0.0.0.0/0
13384 1079K ufw-after-input all -- * * 0.0.0.0/0 0.0.0.0/0
2445 163K ufw-after-logging-input all -- * * 0.0.0.0/0 0.0.0.0/0
2445 163K ufw-reject-input all -- * * 0.0.0.0/0 0.0.0.0/0
2445 163K ufw-track-input all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
362 16596 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 ACCEPT all -- ppp+ ppp+ 0.0.0.0/24 192.168.42.0/24
0 0 ACCEPT all -- ppp+ ppp+ 192.168.42.0/24 0.0.0.0/24
344 29047 ACCEPT all -- ppp+ ppp+ 192.168.42.0/24 172.20.168.0/24
476 74499 ACCEPT all -- ppp+ ppp+ 192.168.125.0/24 192.168.42.0/24
641 39905 ACCEPT all -- ppp+ ppp+ 192.168.42.0/24 192.168.125.0/24
63115 114M ACCEPT all -- eth0 ppp+ 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
96728 8340K ACCEPT all -- ppp+ eth0 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- ppp+ ppp+ 192.168.42.0/24 192.168.42.0/24
0 0 ACCEPT all -- eth0 * 0.0.0.0/0 192.168.43.0/24 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- * eth0 192.168.43.0/24 0.0.0.0/0
2215 293K ufw-before-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
2215 293K ufw-before-forward all -- * * 0.0.0.0/0 0.0.0.0/0
1613 96831 ufw-after-forward all -- * * 0.0.0.0/0 0.0.0.0/0
1613 96831 ufw-after-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
1613 96831 ufw-reject-forward all -- * * 0.0.0.0/0 0.0.0.0/0
1613 96831 ufw-track-forward all -- * * 0.0.0.0/0 0.0.0.0/0
1613 96831 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 1 packets, 116 bytes)
pkts bytes target prot opt in out source destination
283K 262M ufw-before-logging-output all -- * * 0.0.0.0/0 0.0.0.0/0
283K 262M ufw-before-output all -- * * 0.0.0.0/0 0.0.0.0/0
770 59547 ufw-after-output all -- * * 0.0.0.0/0 0.0.0.0/0
770 59547 ufw-after-logging-output all -- * * 0.0.0.0/0 0.0.0.0/0
770 59547 ufw-reject-output all -- * * 0.0.0.0/0 0.0.0.0/0
770 59547 ufw-track-output all -- * * 0.0.0.0/0 0.0.0.0/0
Chain f2b-sshd (1 references)
pkts bytes target prot opt in out source destination
20 1156 REJECT all -- * * 119.90.39.158 0.0.0.0/0 reject-with icmp-port-unreachable
35772 2390K RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-after-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-input (1 references)
pkts bytes target prot opt in out source destination
9577 747K ufw-skip-to-policy-input udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:137
74 16946 ufw-skip-to-policy-input udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:138
11 548 ufw-skip-to-policy-input tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:139
21 1028 ufw-skip-to-policy-input tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:445
14 4632 ufw-skip-to-policy-input udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:67
0 0 ufw-skip-to-policy-input udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:68
1242 146K ufw-skip-to-policy-input all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST
Chain ufw-after-logging-forward (1 references)
pkts bytes target prot opt in out source destination
422 25371 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] "
Chain ufw-after-logging-input (1 references)
pkts bytes target prot opt in out source destination
2411 161K LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] "
Chain ufw-after-logging-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-forward (1 references)
pkts bytes target prot opt in out source destination
602 196K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 3
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 4
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 11
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 12
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
1613 96831 ufw-user-forward all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-before-input (1 references)
pkts bytes target prot opt in out source destination
54 3324 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ufw-logging-deny all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 3
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 4
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 11
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 12
530 27946 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68
18289 1373K ufw-not-local all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT udp -- * * 0.0.0.0/0 224.0.0.251 udp dpt:5353
0 0 ACCEPT udp -- * * 0.0.0.0/0 239.255.255.250 udp dpt:1900
18289 1373K ufw-user-input all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-before-logging-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-logging-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-logging-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-output (1 references)
pkts bytes target prot opt in out source destination
349 36371 ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0
282K 262M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
770 59547 ufw-user-output all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-logging-allow (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW ALLOW] "
Chain ufw-logging-deny (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID limit: avg 3/min burst 10
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] "
Chain ufw-not-local (1 references)
pkts bytes target prot opt in out source destination
7382 458K RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type MULTICAST
10907 915K RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST
0 0 ufw-logging-deny all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-reject-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-reject-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-reject-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-skip-to-policy-forward (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-skip-to-policy-input (7 references)
pkts bytes target prot opt in out source destination
10939 916K DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-skip-to-policy-output (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-track-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-track-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-track-output (1 references)
pkts bytes target prot opt in out source destination
7 524 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW
706 53027 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW
Chain ufw-user-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-user-input (1 references)
pkts bytes target prot opt in out source destination
4871 291K ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:22
4 192 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53
30 1930 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53
Chain ufw-user-limit (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 5 LOG flags 0 level 4 prefix "[UFW LIMIT BLOCK] "
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain ufw-user-limit-accept (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-user-logging-forward (0 references)
pkts bytes target prot opt in out source destination
Chain ufw-user-logging-input (0 references)
pkts bytes target prot opt in out source destination
Chain ufw-user-logging-output (0 references)
pkts bytes target prot opt in out source destination
Chain ufw-user-output (1 references)
pkts bytes target prot opt in out source destination
-
nat
Chain PREROUTING (policy ACCEPT 40331 packets, 2639K bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 5456 packets, 328K bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 775 packets, 60021 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 1141 packets, 81902 bytes)
pkts bytes target prot opt in out source destination
12853 767K MASQUERADE all -- * eth0 192.168.42.0/24 0.0.0.0/0
0 0 MASQUERADE all -- * eth0 192.168.43.0/24 0.0.0.0/0 policy match dir out pol none
1 56 MASQUERADE all -- * eth0 192.168.125.0/24 0.0.0.0/0
-
US 服务器 firewall 规则
控制台安全组已放行全部端口。Mangle 无规则。
其他
CN 和 US 之间互联本来想用 Gre over IPsec 的,但是 Gre 怎么也起不来,遂放弃,选用 L2TP 互联。
不知道有没有更好的互联方法,可以回复告诉我。
排版和写内容花了一个小时……
第 1 条附言 · 2018-07-30 13:43:07 +08:00
散了吧,我发现我把 0.0.0.0/0 写成 0.0.0.0/24 了。
手动狗头
手动狗头
1
Laynooor OP 更正:
从 CN 客户端 A 进行 ping 测试:114.114.114.114 路由为: 192.168.42.1 -> 空路由 |
2
Laynooor OP tail -f /var/log/syslog 看到这个:
Jul 30 13:03:58 vm719214 kernel: [78472.868822] [UFW BLOCK] IN=ppp1 OUT=ppp0 MAC= SRC=192.168.42.10 DST=114.114.114.114 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=59046 DF PROTO=TCP SPT=38030 DPT=443 WINDOW=65535 RES=0x00 SYN URGP=0 但不知道是哪条规则引起的。 |