这是一个创建于 2099 天前的主题,其中的信息可能已经有所发展或是发生改变。
使用 Let's Encrypt 证书,在阿里云 ECS Nginx 开启 https 。
网站首次打开 waterfall 如下,紫色部分 SSL 花费时间太长了,可能的原因是什么?怎么解决?
1. Waterfall
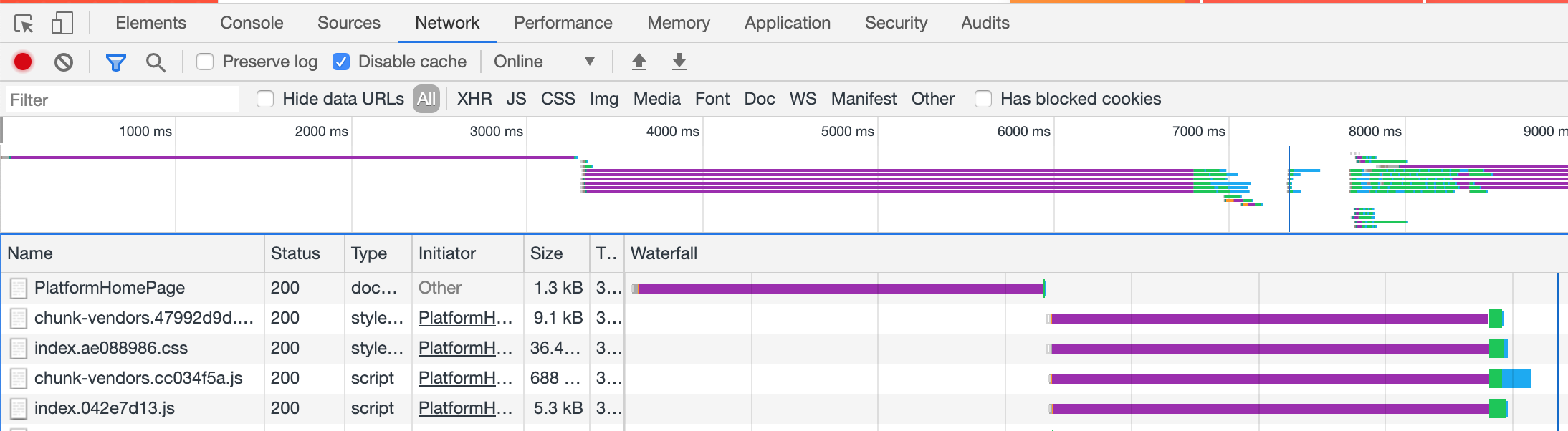
2. 首页 waterfall 详情
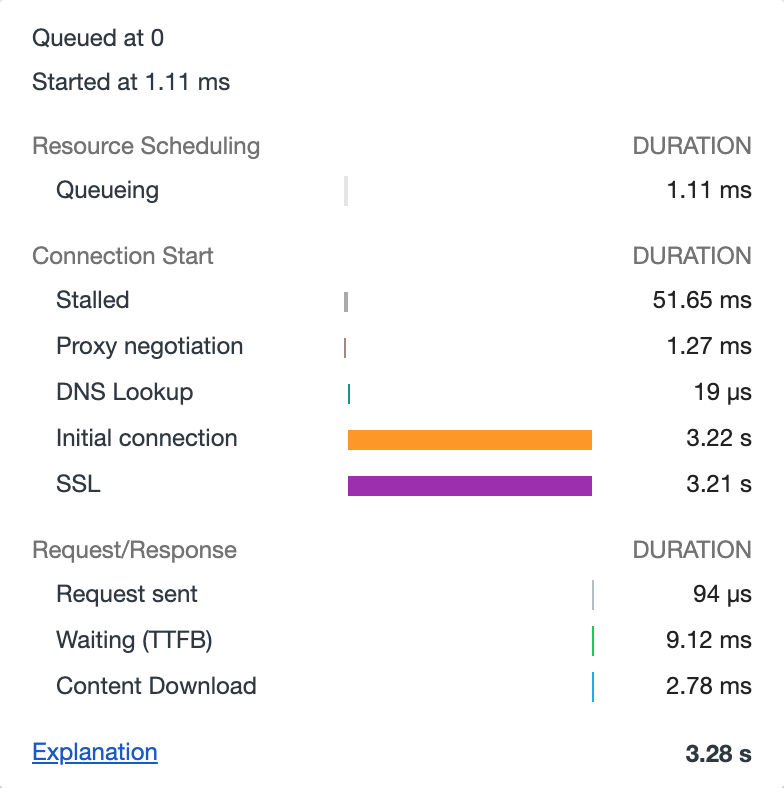
网站绝大部分时间都花在了 SSL 部分了。
第 1 条附言 · 2020 年 5 月 20 日
谢谢大家的帮助,现在总结一下:
一、原因:Let's Encrypt OCSP 域名地址被污染,国内无法访问。
二、解决方案:
1 )购买通用域名,省心
2 )使用阿里云免费 DV 单域名证书
缺点:由于是单域名证书,每个域名都需要申请对应的证书,在一台服务器上部署多个服务时就有问题,比如:
server {
listen 443 ssl;
server_name aaa.com;
ssl_certificate aaa.com.crt;
}
server {
listen 443 ssl;
server_name bbb.org;
ssl_certificate bbb.org.crt;
}
问题的详细信息和解决方案,参考 http://nginx.org/en/docs/http/configuring_https_servers.html 中的 “Name-based HTTPS servers”
3 )开启 OCSP Stapling
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem;
resolver 8.8.8.8 8.8.4.4 216.146.35.35 216.146.36.36 valid=60s;
resolver_timeout 2s;
#### 或者 ####
ssl_stapling on;
ssl_stapling_verify on;
ssl_stapling_file /path/to/ocsp_res.crt;
一、原因:Let's Encrypt OCSP 域名地址被污染,国内无法访问。
二、解决方案:
1 )购买通用域名,省心
2 )使用阿里云免费 DV 单域名证书
缺点:由于是单域名证书,每个域名都需要申请对应的证书,在一台服务器上部署多个服务时就有问题,比如:
server {
listen 443 ssl;
server_name aaa.com;
ssl_certificate aaa.com.crt;
}
server {
listen 443 ssl;
server_name bbb.org;
ssl_certificate bbb.org.crt;
}
问题的详细信息和解决方案,参考 http://nginx.org/en/docs/http/configuring_https_servers.html 中的 “Name-based HTTPS servers”
3 )开启 OCSP Stapling
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem;
resolver 8.8.8.8 8.8.4.4 216.146.35.35 216.146.36.36 valid=60s;
resolver_timeout 2s;
#### 或者 ####
ssl_stapling on;
ssl_stapling_verify on;
ssl_stapling_file /path/to/ocsp_res.crt;
1
lavvrence 2020 年 5 月 18 日
看一下 conf
|
2
lavvrence 2020 年 5 月 18 日
curl 网站 https 地址 -vvv
|
3
Tink PRO 上 cdn
|
4
rrfeng 2020 年 5 月 18 日
估计是 CA 验证在国外导致的,nginx 配置一下 ocsp stapling 吧。
|
5
jacklin96 2020 年 5 月 18 日
OCSP 域名被污染了,需要换证书或者客户端翻墙
可能直接换证书最快 加 OCSP Stapling 也不一定有效 |
6
constructor OP @jaylee4869
### 1. ngxin.conf 配置如下 ```conf user www-data; worker_processes auto; pid /run/nginx.pid; events { worker_connections 768; # multi_accept on; } http { ## # Basic Settings ## sendfile on; tcp_nopush on; tcp_nodelay on; keepalive_timeout 65; types_hash_max_size 2048; # server_tokens off; # server_names_hash_bucket_size 64; # server_name_in_redirect off; include /etc/nginx/mime.types; default_type application/octet-stream; ## # SSL Settings ## ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE ssl_prefer_server_ciphers on; ## # Logging Settings ## access_log /var/log/nginx/access.log; error_log /var/log/nginx/error.log; ## # Gzip Settings ## gzip on; gzip_disable "msie6"; gzip_vary on; gzip_proxied any; gzip_comp_level 6; gzip_buffers 16 8k; gzip_http_version 1.1; gzip_types text/plain text/css application/json application/javascript text/xml application/xml application/xml+rss text/javascript; ## # Virtual Host Configs ## include /etc/nginx/conf.d/*.conf; include /etc/nginx/sites-enabled/*; } ``` ### 2. 网站 dev.example.com 配置如下: ```conf server { listen 80; listen [::]:80; server_name dev.example.com; location / { proxy_set_header X-Forwarded-For $remote_addr; proxy_set_header Host $http_host; proxy_set_header X-Forwarded-Proto https; proxy_pass http://112.74.113.106:8090; } listen [::]:443 ssl; # managed by Certbot listen 443 ssl; # managed by Certbot ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; # managed by Certbot include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot } ```conf ### 3. curl -vvv https://dev.example.com 输出如下: ```conf * Rebuilt URL to: https://dev.example.com/ * Trying 112.74.90.77... * TCP_NODELAY set * Connected to dev.example.com (112.74.90.77) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * TLSv1.2 (OUT), TLS handshake, Client hello (1): * TLSv1.2 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Client hello (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS change cipher, Client hello (1): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-RSA-CHACHA20-POLY1305 * ALPN, server accepted to use http/1.1 * Server certificate: * subject: CN=*.example.com * start date: Apr 29 13:04:41 2020 GMT * expire date: Jul 28 13:04:41 2020 GMT * subjectAltName: host "dev.example.com" matched cert's "*.example.com" * issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3 * SSL certificate verify ok. > GET / HTTP/1.1 > Host: dev.example.com > User-Agent: curl/7.54.0 > Accept: */* > < HTTP/1.1 200 OK < Server: nginx/1.14.0 (Ubuntu) < Date: Mon, 18 May 2020 10:38:26 GMT < Content-Type: text/html < Content-Length: 2878 < Last-Modified: Sun, 17 May 2020 10:44:30 GMT < Connection: keep-alive < ETag: "5ec1158e-b3e" < Accept-Ranges: bytes ``` * 域名和 IP 进行了替换,还请谅解。 * |
7
constructor OP @jacklin96
"更换证书"是指换其他 CA 比如 Symantec 、GlobalSign 、GeoTrust 还是用 Let's Encrypt 重新生成证书? |
8
n329291362 2020 年 5 月 18 日
let's encrypt 的证书 服务端配置一下 ocsp stapling 吧
或者买其他家的证书 就是买 Symantec 、GlobalSign 、GeoTrust 之类的 |
9
cy476571989 2020 年 5 月 18 日
我也有同样的问题。
|
10
shinciao 2020 年 5 月 18 日
开一下 ocsp 装订试试 虽然我觉得可能没用 chrome 应该是不检查 ocsp 的
|
11
xiaotianhu 2020 年 5 月 18 日 via iPhone
ocsp 服务器坏了
被迫换了阿里云免费证书。 |
12
constructor OP OCSP 服务器连接不上, ping ocsp.int-x3.letsencrypt.org 超时
通过 openssl 验证超时: ``` openssl ocsp -issuer fullchain.pem -cert cert.pem -text -url http://ocsp.int-x3.letsencrypt.org OCSP Request Data: Version: 1 (0x0) Requestor List: Certificate ID: Hash Algorithm: sha1 Issuer Name Hash: 7EE66AE7729AB3FCF8A220646C16A12D6071085D Issuer Key Hash: 25AA0A105713B51AB5A49554679566211FA63FCF Serial Number: 03638E20AC5D648DA7DB51EA00638CFAEF33 Request Extensions: OCSP Nonce: 0410053BDB6861C216D9924BC81A9295430F Error connecting BIO Error querying OCSP responder 4733388396:error:02FFF03C:system library:func(4095):Operation timed out:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.260.1/libressl-2.6/crypto/bio/bss_conn.c:244:host=ocsp.int-x3.letsencrypt.org:80 4733388396:error:20FFF067:BIO routines:CRYPTO_internal:connect error:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.260.1/libressl-2.6/crypto/bio/bss_conn.c:247: ``` |
13
jacklin96 2020 年 5 月 19 日
@constructor 换其他 CA 就行,国内目前只能远离 Let's Encrypt
|
14
BitCert 2020 年 5 月 19 日
LE 现在不稳定
|